Install a certificate with Microsoft IIS8.X+ and Windows Server 2012+.
Retrieve your certificate on your server
You can only use this method if you generated your CSR on Windows. If you used our tool Keybot, please consult our pfx importation guide.
- Retrieve your certificate in format p7b (global install file) by following the link provided in the delivery email or via your certificate status page.
- Create/move the p7b file on your server.
Import the certificate
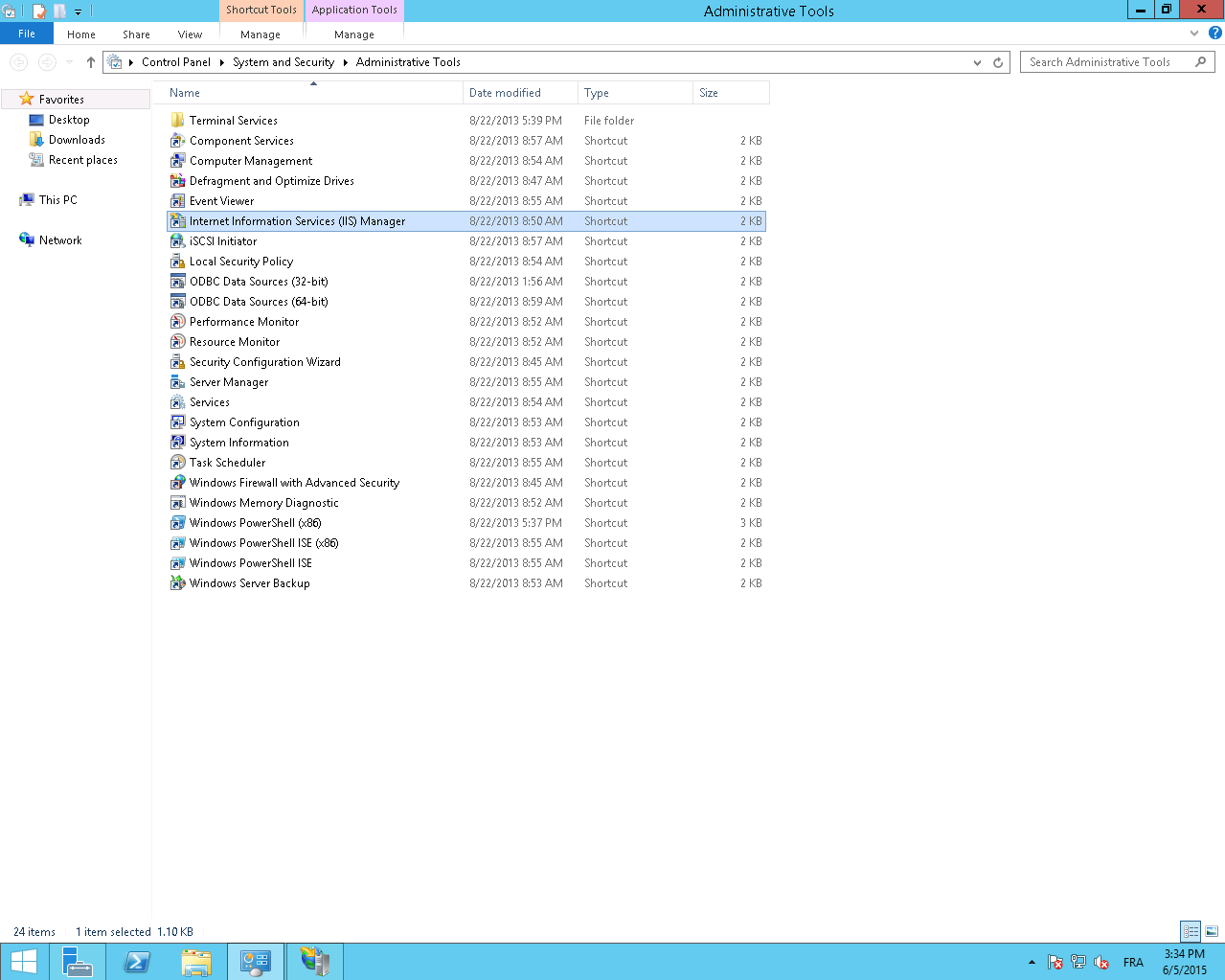
- Launch Internet Information Services (IIS) Manager from Administrative tools.
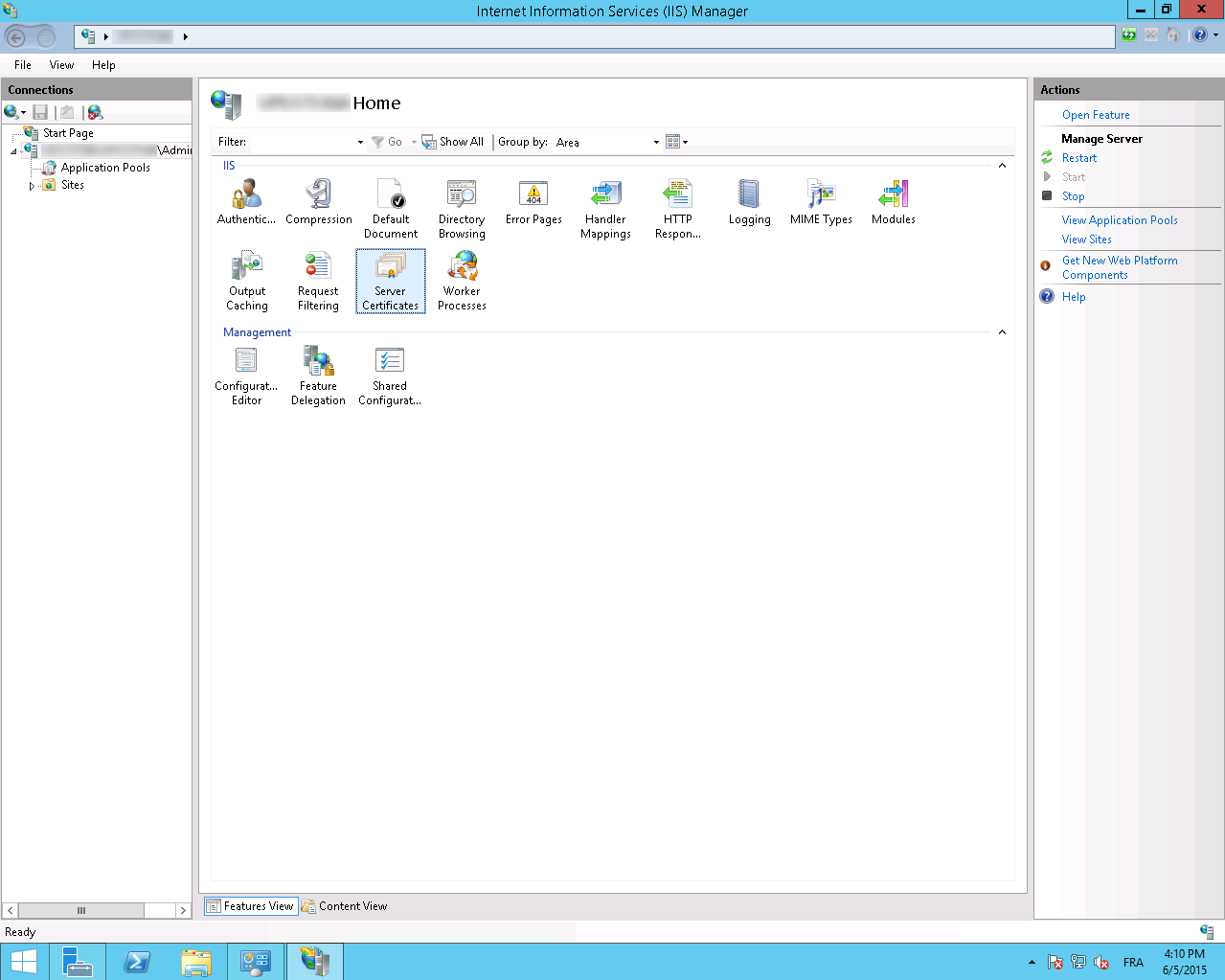
- Select Server Certificates
- Select Complete Certificate Request in the menu Actions menu of the right window.
- Then select your p7b file and give it a recognizable name and a store.
- Then validate to add your certificate.
- It should now be available in your certificates list.
Link the certificate
- In Internet Information Services (IIS) Manager, select your website.
- Select the Bindings option of the Actions located on the right side of the window.
- Then select Add
- Then select HTTPS and the previously added certificate.
SNI case
If you need to install several certificates for different domains with the same IP address, you need to activate the SNI protocol by enabling the "Require server name indication" checkbox.
Possible error
It is possible that when you activate the SNI, and your installation is correct, the certificate presented by your server is not the right one and the SSL_ERROR_BAD_CERT_DOMAIN error is displayed.
In this case, it is necessary to check that there are no old certificates or bindings that could interfere with the proper functioning of the server.
- In the certificates MMC, in the personal folder, check that you only have valid certificates. If necessary, export the expired certificates with the private key, and then delete them from the MMC.
- Start a command prompt with Administrator rights, and type the following command:
netsh http show sslcertThis command lists all active bindings between your certificate(s) and the associated domain(s).
If in the list of bindings, one of the certificates is attached to an IP address, it is not good. Here is an example:
IP address:port : 192.168.2.1:443
...
...
You must remove this link with the following command:
netsh http delete sslcert ipport={localIPAddress}:{port}
Using the example above, this gives:
netsh http delete sslcert ipport=192.168.2.1:443
Security recommendations
- We recommand to disable SSLv2 and SSLv3 protocols.
- We recommend enabling HSTS (IIS configuration).
- Pour mitiger les risques de sécurité liés à la configuration de Diffie-Helman et à la faille de sécurité Logjam, nous vous recommendons de configurer les Cipher Suites de IIS. Pour plus d'informations, consultez la this documentation and this Microsoft documentation as well as the Mozilla recommendations related to compatibility. (to be used as an indication, the latter not being compatible with IIS, contrary to the two previous links).
- We also recommend disabling the RC4 and 3DES encryption algorithms. See our documentation.
And discover IIS Crypto by NARTAC, a toolthat will help you do modifications in IIS (compatible with IIS6).
The is also a powershell script aloowing to apply all those security recommandations: external link.
Useful links
- Generate a private key and a CSR on a Microsoft server (IIS8+ / Windows Server 2012+)
- Export your certificate and its private key to a Microsoft server (IIS8+ / Windows Server 2012+)
- Import a PKCS#12 (.pfx/.p12) certificate on a Microsoft server (IIS8+ / Windows Server 2012+)
- Disable an Intermediate or Root Certificate on Windows Server
- Creating a directory starting with a dot on windows